It was our goal to change things, hopefully for the better.
Chapter 1: Your System, Its Mission, “O–I–F”, and
Enablers
In this chapter, the sustainment management model is covered
from a big picture view. Following chapters provide additional details.
Everything Starts and Ends with Risk Identification
The “I” in O-I-F” is “identify risks”. Everything in the
sustainment management model, as described in this book, is tightly connected
to the sustainment risk identification process. It is the very heart of
effective weapon system sustainment. Chapter 4 explains the sustainment risk
identification process.
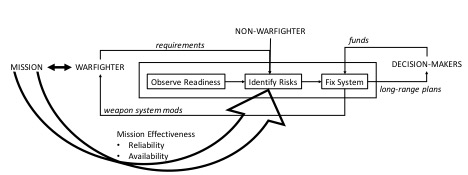
As the block diagram above implies, risk identification is
the link between observations of system degradation and plans (fixes) designed
to reverse the degradations. To identify risks, the system must be observed.
Once risks are identified, planning begins to try to mitigate them.
The right side of the diagram above shows that the risk
identification process directly feeds the process to create long-range plans
and obtain funds, priority, and authority to execute. Once execution starts, if
the fixes you are trying to implement are not working out, another trip to the
risk board is in order.
System assessment (observing readiness) is certainly
important and must stand alone as a program that continuously watches your
system. However, the entire reason for the existence of an assessment program
is to feed the risk identification process. As risks are identified in one
area, priorities for assessment in other areas can increase. For instance, if
electronic degradation in a flight control subsystem is found and a risk is
written, increased scrutiny will most certainly be directed to electronics
assemblies throughout the system. And if your ability to observe is lacking,
you can write a risk to address it.
This diagram also identifies a group of people key to weapon
system assessment, the warfighters. Warfighters have a mission that is achieved
by use of their weapon system. To apply this to the civilian world, a
“warfighter” and “mission” must be identified that your system satisfies.
Risk identification is also where the warfighter finds their
strongest voice as risks are considered in light of the mission. The meta-model
diagram above (see also chapter 2) shows reliability and availability as
mission readiness factors, but other readiness factors will also exist in your
system. Risk identification generates important arguments concerning what is
part of and what is not part of your system.


No comments:
Post a Comment